VMware has just released Express patches on Bash code injection Vulnerability aka “ShellShock” for most of the VMware products. However, this post is focused on express patches @vCenter Server Virtual Appliance.
Note:Please do read KBs referred below carefully corresponding to each express patch release which addresses bash vulnerability. Also note that Bash code injection vulnerability does NOT affect Windows based vCenter server.
Express patch is released on each release lines i.e. 5.0.x, 5.1.x, 5.5.x
If you are running vCenter Server Appliance 5.0.x, vCenter Server Appliance 5.0 U3b addresses Bash vulnerability:
KB:vCenter Server Appliance 5.0 U3b KB
Download from here:vCenter server appliance 5.0 U3b (Scroll down to 5.0 U3b)
If you are running vCenter Server Appliance 5.1.x, vCenter Server Appliance 5.1 U2b addresses Bash vulnerability:
KB:vCenter Server Appliance 5.1 U2b KB
Download from here:vCenter Server Appliance 5.1 u2b (Scroll down to 5.1 U2b)
If you are running vCenter Server Appliance 5.5.x, vCenter Server Appliance 5.5 U2b addresses Bash vulnerability:
KB: vCenter Server Appliance 5.5 U2a KB
Download from here:vCenter Server Appliance 5.5 U2a (Scroll down to 5.5 U2a)
VMware KB on Bash bug assessment :VMware KB on Bash Code Injection Assessment
VMware Security Advisory on Bash bug :VMware Security Advisory (Here you can also get patch details @ other VMware products)
How to quickly reproduce this bug (before applying the patch):
1. Login /SSH to the vCenter server virtual appliance through Putty.
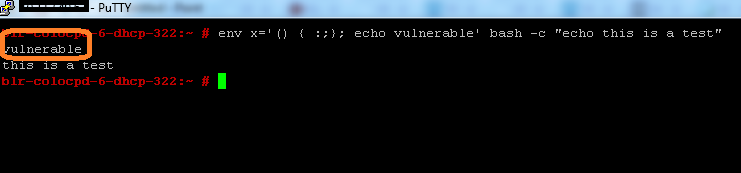
2. Run this bash script :”env x='() { :;}; echo vulnerable’ bash -c “echo this is test”. It should display output as follows :
You could see both “vulnerable & “this is test” are displayed as output.
How to quickly verify this bug (after applying the patch):
1. Login /SSH to the vCenter server virtual appliance through Putty.
2. Run same bash script :”env x='() { :;}; echo vulnerable’ bash -c “echo this is test”.It should display output as follows :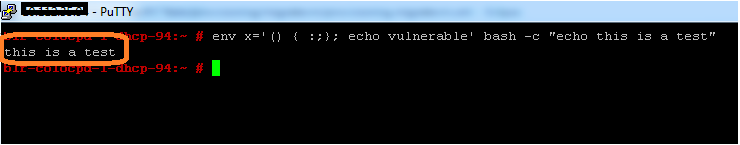
You could see only “this is test” is displayed as output. “vulnerable” should not be displayed with patch.
Learn more about Bash code injection:The Bash bug Explained

Vikas Shitole is a Staff engineer 2 at VMware (by Broadcom) India R&D. He currently contributes to core VMware products such as vSphere, VMware Private AI foundation and partly VCF . He is an AI and Kubernetes enthusiast. He is passionate about helping VMware customers & enjoys exploring automation opportunities around core VMware technologies. He has been a vExpert since last 11 years (2014-24) in row for his significant contributions to the VMware communities. He is author of 2 VMware flings & holds multiple technology certifications. He is one of the lead contributors to VMware API Sample Exchange with more than 35000+ downloads for his API scripts. He has been speaker at International conferences such as VMworld Europe, USA, Singapore & was designated VMworld 2018 blogger as well. He was the lead technical reviewer of the two books “vSphere design” and “VMware virtual SAN essentials” by packt publishing.
In addition, he is passionate cricketer, enjoys bicycle riding, learning about fitness/nutrition and one day aspire to be an Ironman 70.3